Cyber Security Awareness Month 2023
October is Cyber Security Awareness Month, a time for everyone to enhance their cyber security knowledge and take proactive steps to safeguard their information and devices.
This international initiative aims to raise awareness of the importance of cyber practices and and presents an ideal opportunity to take action to secure your information and devices.
- Cyber threats facing small to medium-sized businesses (SMBs)
Small to medium-sized businesses (SMBs) are particularly susceptible to cyber security risks. Limited resources, expertise, and infrastructure, as well as a lack of awareness and training, make them vulnerable. Many inadvertently engage in risky practices like clicking on suspicious emails, using easily guessable passwords, or neglecting timely software updates. These actions can inadvertently open doors to cyber attackers.
- Cyber threats facing individuals
Individuals, much like SMBs, utilize devices (computers, mobile phones, tablets, and other internet-connected devices) and accounts (email, banking, shopping, social media, gaming, etc.) daily, leaving them exposed to a range of cyber threats in today's digital age. Some of the most prevalent threats include, but are not limited to, phishing attacks, identity theft, data breaches, and online scams.
Moraitis Consulting Joins the Cyber Security Awareness Month Campaign: Be Cyber Wise, Don't Compromise
Moraitis Consulting proudly participates in this year's Cyber Security Awareness Month campaign, themed 'Be cyber wise, don't compromise.' We strongly encourage individuals and businesses to adopt four simple steps to become cyber-wise:
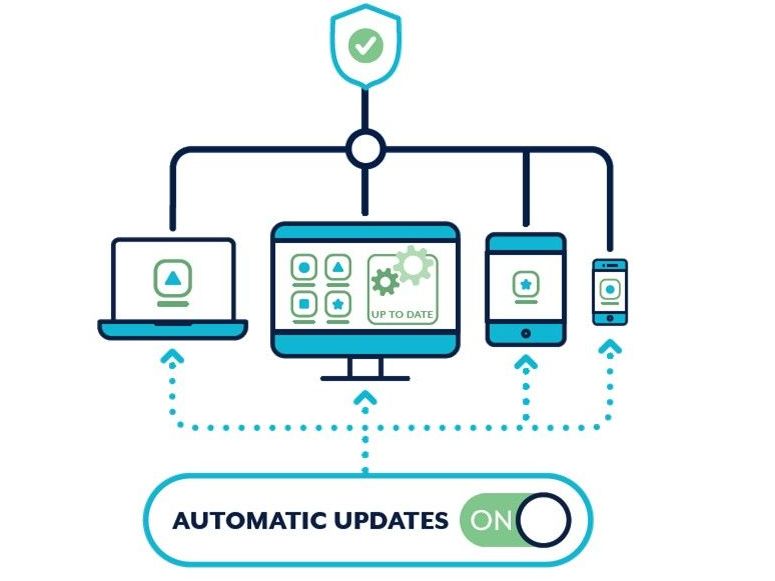

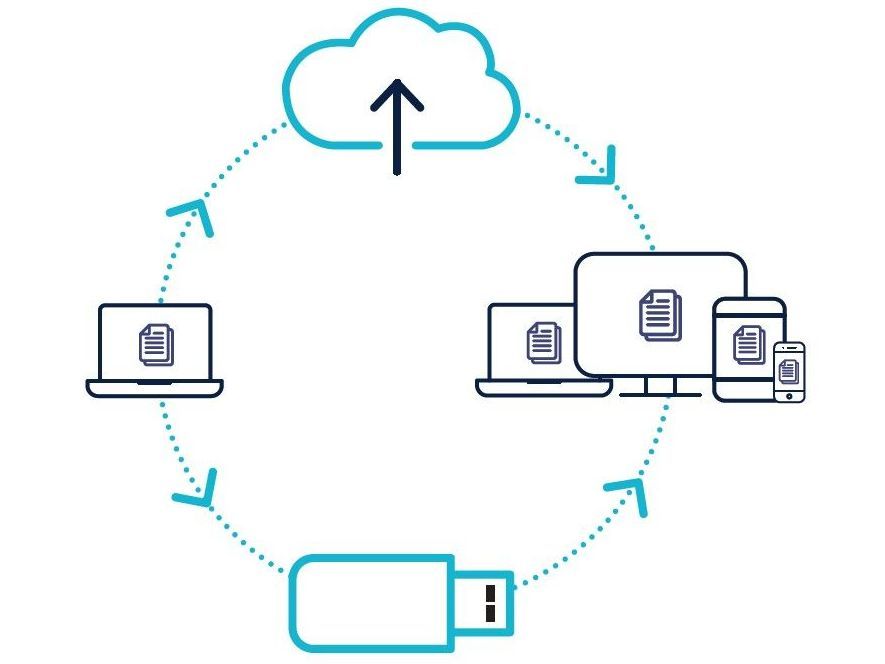
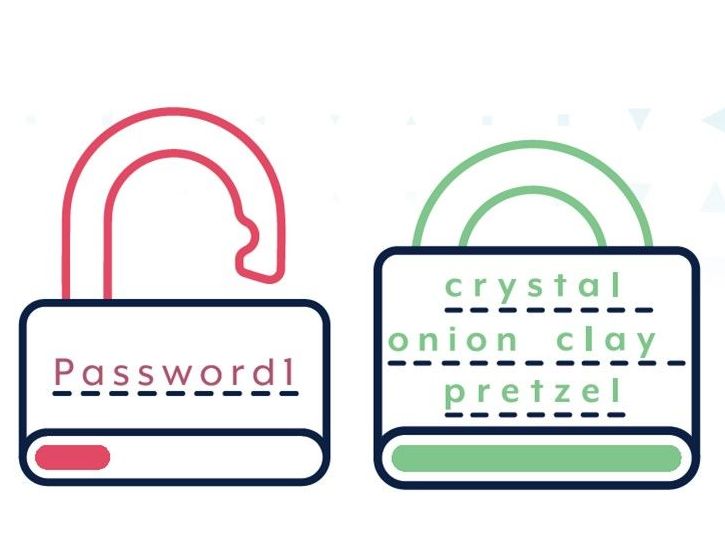
Actions at Moraitis Consulting
At Moraitis Consulting we implement all of the above recommendations, plus we ensure our business’s policies and procedures comply with the cybersecurity framework The Essential Eight Maturity Model developed by the Australian Cyber Security Centre (ACSC).
The Essential Eight Maturity Model is designed to help organisations improve their cybersecurity posture by focusing on eight essential strategies that mitigate cyber threats. These strategies are based on the Centre for Internet Security (CIS) Controls, which are a set of best practices for securing information systems and data.
Here are the eight essential strategies outlined in the Essential Eight Maturity Model:
- Application Whitelisting: This involves only allowing approved applications to run on systems. By preventing unauthorised software from executing, organisations can reduce the risk of malware infections.
- Patch Applications: Keeping software applications up-to-date with the latest security patches helps in addressing known vulnerabilities. Cybercriminals often target outdated software to exploit security flaws.
- Configure Microsoft Office Macro Settings: Cybercriminals frequently use malicious macros in Microsoft Office documents to deliver malware. Configuring correct macro settings can prevent these malicious macros from running.
- User Application Hardening: Restricting the use of unnecessary and potentially vulnerable functionalities within applications can minimise the attack surface. By disabling unnecessary features, organisations can reduce the risk of exploitation.
- Restrict Administrative Privileges: Limiting administrative privileges ensures that only authorised users have access to critical system settings. This reduces the potential impact of malware or malicious activities.
- Patch Operating Systems: Just like patching applications, it's crucial to keep the operating systems up-to-date. Security patches are regularly released to address vulnerabilities in operating systems.
- Multi-Factor Authentication: Implementing multi-factor authentication (MFA) adds an extra layer of security by requiring users to provide multiple forms of identification before accessing accounts or systems. This significantly enhances security, especially in case of stolen or weak passwords.
- Daily Backups: Regularly backing up important data is essential. In the event of a ransomware attack or data loss, having up-to-date backups ensures that critical information can be restored without paying a ransom.
The Essential Eight Maturity Model is not a one-size-fits-all approach. SMBs are encouraged to assess their specific cybersecurity risks, capabilities, and resources, and tailor the implementation of these strategies according to their needs. By adopting these essential strategies, at Moraitis Consulting we can enhance our cybersecurity defences against a wide range of cyber threats.
Additional Recommended Actions

Cybercrime on the Rise: Take Action
Cybercrime reports are increasing, but by taking these simple steps, everyone can play a part in making Australia the most secure place to connect online. The Australian Cyber Security Centre's Annual Threat
Report for 2021-22 revealed a 13% rise in reported cybercrimes compared to the previous year. Frauds, online shopping, and online banking comprised over half of all reports.
If you are concerned about your cyber security, explore resources and guidance from the Australian Cyber Security Centre, where you can find resources and valuable information about how to be cyber-safe.
For comprehensive cyber security assistance, feel free to contact us. Moraitis Consulting is here to support your cyber security needs.
Contact Us











